Eliminate system defects
via Secure System Management Cluster, secure, rapid and reliable back to should-be state
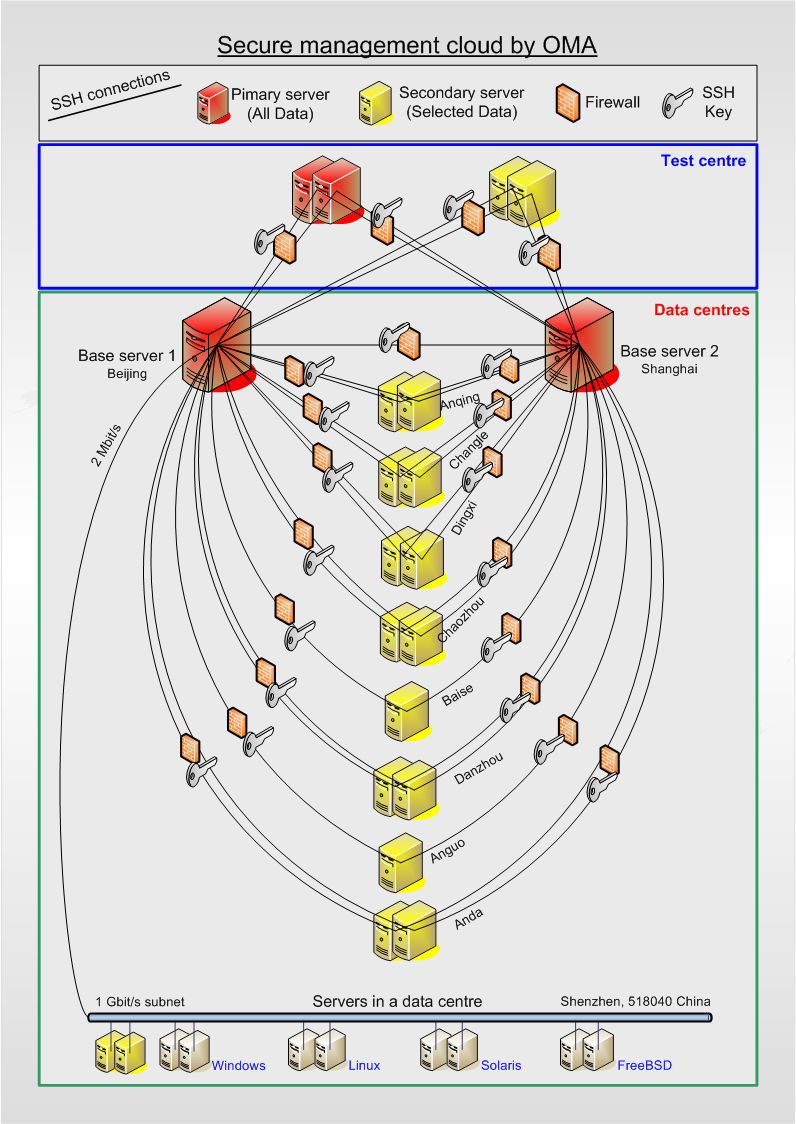
The SSM-Cluster consists of at least two OMA base servers, which are situated at two different secure locations. A sub-network is established between the base servers. Via this network the data transfer within the SSM-Cluster is effected. If required, additional OMA servers are connected to the SSM-Cluster. The communication between the OMA servers and the clients is always delivered through the second network card of the OMA server, since the first card is reserved for data transfer within the SSM-Cluster. Corresponding to security requirements the OMA base servers do not necessarily have to be connected to the clients. According to the locations of OMA servers within the SSM-Cluster, SSM-sub-networks may be called into action. Under such circumstances, it is advisable to choose a Top-Down-structure for transferring data between within the SSM-Cluster. In doing so, the OMA base server accesses all other OMA servers radially, whereas interactions between OMA servers at different locations are prohibited. The only network protocol within the SSM-Cluster is the SSH protocol. The figure below illustrates schematically the structure of a SSM-Cluster in China.